A Case Study in Bad Hiring Practice: And How To Fix It
In this day and age of cybersecurity professionals crying out for roles, we're still seeing companies complain that there is a skills shortage and a lack of talent. A quick scan through your LinkedIn feed will show this is absolute nonsense: there is a mass of experienced, capable talent out there looking for roles. So what's the problem?
There are two main areas where companies are sabotaging the hiring pipeline:
1) Companies that are abusing the job boards and hiring process.
We've all seen these: job adverts asking for the moon on a stick with low pay, so the company can abuse the visa process. Companies lying to their employees about hiring more team members, when they have no intention of cutting into profit margins by actually responding to applications. And companies that are just data mining applicants, stupidly believing that a ghosted candidate is going to magically want to do business with them once they actually have a live role.
2) Companies that are just completely crap at actually hiring.
This is where I'm going to be looking at in this article. Despite years of being told (and shown!) how to change their hiring practices to land good cybersecurity talent, companies still persist in the same, broken, unworkable approaches.
So, for our Case Study of Crapness, please step forward: Canonical.
Canonical has been advertising for a Head of Security Operations role for almost a year now. You'd think the darling of the Linux world would have an endless stream of geeks eager to work for them. And yet: the role is still being advertised. Let's have a look at why they haven't been able to fill it.
Red Flags from the Job Posting
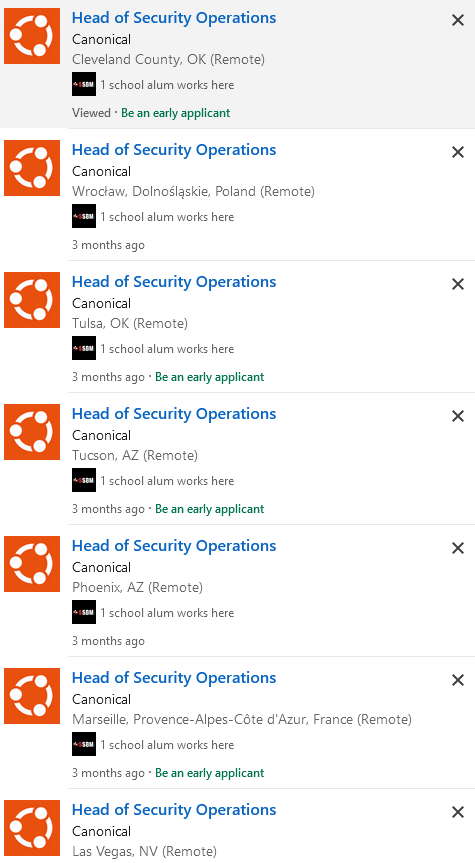
The biggest initial red flag is shitting up the job boards (LinkedIn and elsewhere) by posting exactly the same role for every single European country and US state they are hiring from. Sometimes, for multiple cities within a country (advertising a fully remote role for both Milan and Turin is my favourite here). Any normal person would say "EU-wide, remote role". But no, Canonical have clogged up everyone's searches with their spam.
Head over to their LinkedIn homepage at https://www.linkedin.com/company/canonical/jobs/ and see for yourself.
Any serious candidate is going to have some finely tuned saved job searches, which are now rendered useless because Canonical has spammed 20 or so roles that get picked up by your search parameters.
"It makes the role more visible." "It increases the chances of a candidate seeing the role."
Does it, bollocks. What it does do is make it clear that Canonical doesn't care about anyone else's time or resources, and that their hiring team doesn't understand how to actually advertise a role: just spam away, the more postings the better!
Digging into the actual job advert, we can see a couple of other obvious red flags. The spelling mistakes are one: unforgivable in this age of AI tools plugged into literally everything.
"Experience with security posture management of corporate endpoitns" isn't just in the hundreds of spammed job postings - it's also in the role description on Canonical's actual recruiting website as well. Excellent job.
Also, there is no target salary or salary range. This is a red flag for a couple of reasons:
- It sends a message that the actual compensation is going to be rubbish.
- It sends a message (combined with the evidence from the advert spamming) that the hiring company will be paying different levels of compensation based on where the applicant lives.
That last one is particularly inexcusable. We call it a 'compensation package' for a reason: the employer is compensating the employee for using their expertise, time, and energy to make the employer money. It has nothing to do with the CoL where you live, and everything to do with how much the company values you in that role.
If my cost of living is 40% less in Italy than it is in London, and therefore I get paid 40% less, does that mean it's OK for me to give 40% less effort? If a company thinks they can pay different rates for the same skillset if you live in Milan instead of Frankfurt, they are demonstrating that they do not value the employee. They are a replaceable cog in their machine with a price tag.
Finally, there are some massive red flags in the actual requirements for the role. I'm going to call out one specifically:
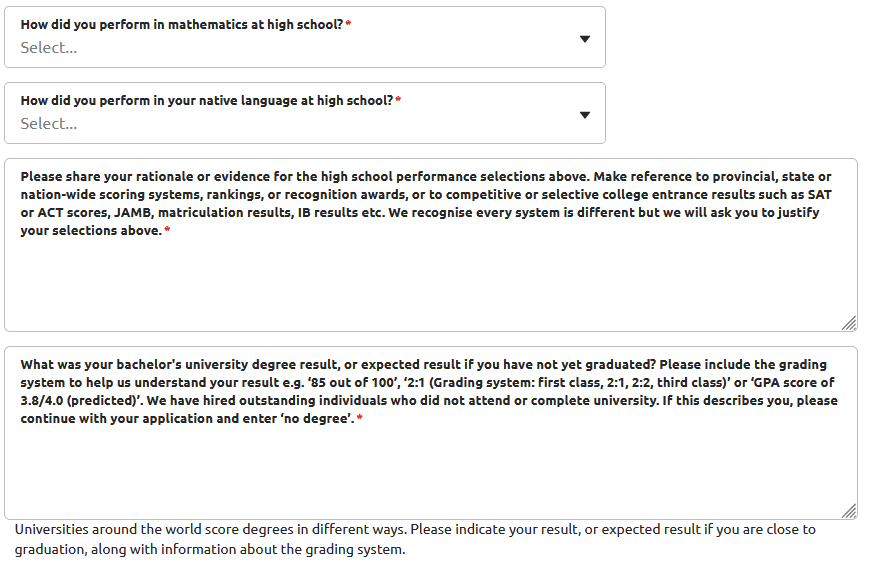
An exceptional academic track record from both high school and university
What the hell is this? There is so little relevance from what was studied at school at 16 years old to a Head of Security Operations role that we'd have to invent entire new fields of science just to measure it. What utter rubbish.
I've written at length in other articles about how demanding a degree for cybersecurity roles is not just irrelevant, but it blocks some of the best candidates. But high school? Who got paid to write that? And why aren't they now unemployed?
Initial Application Process
Any company that uses Workday needs to fire their entire HR department. We all know why, we've all had to deal with it:
- "Upload your CV"
- "Now manually fill in 3-4 pages of *exactly the same information*, because we don't value your time"
- "Now enter some demographic information which has zero relevance to your application but gives us some stats so we can feel good about ourselves."
Canonical's application process is, unbelievably, even more shitty than this. Much like Satan himself, I have some genuine respect for anyone who can come up with something worse than Workday. If you head to their application page on Greenhouse.io, there's the usual "Upload your CV", "Give us your basic details" stuff.
Then we head off the rails of reasonableness and into the realm of madness.
Let's be clear: this is an initial application. Any reasonable candidate expects that this is the filtering process: what are we asking for, what's on your CV, does it match - yes, line up an interview.
The interview is where the actual questioning to dig into a candidate's knowledge happens, and (unless your company is crap at hiring) should be conducted by the line manager, or at the very least, a subject matter expert.
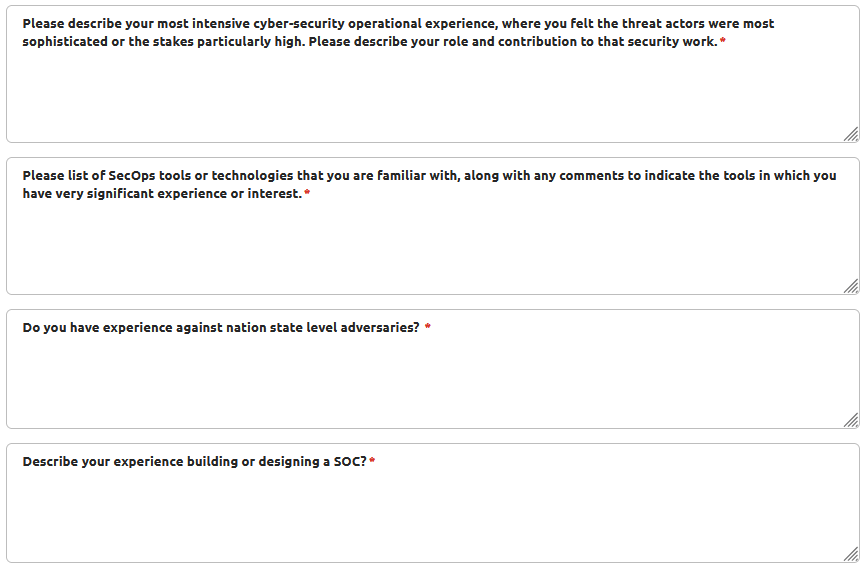
But no. Canonical is asking in-depth questions about experience that belong firmly in an interview.
No. These are questions that have nuance and context that cannot be answered in a character-limited text field, and absolutely should not be reviewed by a hiring manager or member of the HR team.
Any actual competent candidate would look at nonsense like that, say "Stuff that, I'm out" and close their browser window. This is an absolutely cretinous thing to be asking at this stage of an application (the application! Not even an interview!).
Given this is a "Head of" role, reporting to senior leadership, anyone in that role with a pulse and at least two brain cells to rub together would understand how self-defeating asking these sorts of questions in an application is.
But it gets worse.
I was scathing about their requirement in the job advert for "an exceptional academic track record from both high school and university". Here, Canonical is doubling down on their idiocy.
None of this - none of it at all - is remotely relevant to the actual day-to-day job of a Head of Security Operations. Again, these are questions that cannot be answered appropriately in character-capped text fields. But beyond that, these are questions that should not - ever - be used to screen applicants. Applicants for a role where these requirements are not even remotely relevant.
How Their Interview Process Works
Having waded through this nonsense, your application finally gets sent. As with many companies, Canonical sends a little follow-up email to let you know what the actual interview process will look like.
If the application process didn't put you off, then this will be the final nail in the coffin for your application.
First off, your application does not get reviewed by someone from HR, or a hiring manager, or even the line manager for the role. No.
"A senior team of managers and leaders from across the company form a virtual team of hiring leads to shepherd every application through our process. They are not recruiters"
Your application is going to be reviewed by a random group of people who have nothing whatsoever to do with the role, who will not have relevant expertise to judge what a "good" application looks like, and who are clearly hiring for clique-fit rather than competency.
Huge red flag: this hiring-by-committee approach never, ever approves of top candidates. Because a company where someone from a random department gets to review your application is a company that has mediocre chair warmers in senior positions, who want to ensure there are no pockets of excellence in the business that could show them up. Good leaders hire people better than themselves: committees hire mediocrity to cover their arses.
The biggest fail, though, the absolute discriminatory process that guarantees neuro-divergent or anyone with mental health issues will be weeded out, is the use of aptitude and personality tests.
"Our interview process starts with a written interview, which will be reviewed in an anonymized queue to reduce bias, and a standardised assessment of aptitude and personality, to provide a more objective initial application review."
Aptitude and personality tests have been snake oil since they were introduced, and they remain an incredibly stupid and ineffectual way to assess a candidate. There have been decades of research explaining why they suck, and why the people who use them are idiots. Don't just take my word for it, have a look through the detailed investigation the Harvard Business Review did on it - *over a decade ago*. https://archive.ph/p2Frg
The other major problem with aptitude and personality tests is that they also immediately disqualify anyone who is neuro-divergent, who are exactly the sort of people any sensible organisation would want to attract to a cybersecurity role. This is not just sabotage of the hiring process: this is demonstrable ignorance and incompetence from everyone involved in the hiring process.
If you thought Canonical's statement on Diversity https://canonical.com/careers/company-culture/diversity was just another instance of cloying, corporate bullshit - well, now you have the evidence.
In this day and age of increasingly sophisticated phishing and fake hiring scams, it's also good to see that Canonical will openly enable scamming of applications by having a mish-mash of external companies involved:
"As you move through the process you will receive a series of communications from us. These will come directly from our Applicant Tracking System (Greenhouse), our partner providers (Thomas International and Devskiller) or as an email from your hiring lead here."
Why? Why would you do this? The only communication applicants should be getting is from the nominated HR person or hiring manager who is managing your application. Random emails from three external parties or a random employee are just begging for some social engineering. This is doubly obnoxious when you're trying to hire for a security role.
Final Thoughts
You may think I'm being overly harsh to Canonical, and that I'm making some indefensible judgements. And you could be right - so don't take my word for it.
Something everyone should be doing before even thinking about applying for a role is heading over to Glassdoor, and looking at two things:
- what applicants are saying about the hiring process
- what employees are saying about the company
Glassdoor is a good barometer for company health because essentially the reviews break things down into three main areas:
- There's not enough information
If there are only 1 or 2 reviews (which we'd expect for a smaller company or a startup), it's hard to get a feel for the company. Someone might have been fired for taking a dump in the microwave, and left a scathing review. Or there might only be 12 employees, and only 1 person could be bothered to write up their thoughts.
- There are several reviews, and they're generally positive
Everyone likes to whine and complain, so there will always be some negative sentiment, but in general, what we want to see is several balanced reviews, with some positives and negatives, and some good reasons why. Companies with this sort of profile on Glassdoor are generally going to be OK, with nothing more serious than the usual everyday corporate nonsense we all have to endure.
- There are a load of very negative reviews, and a load of hugely positive reviews
These are the toxic hell-holes. The negative reviews come from the long stream of dissatisfied employees who are venting their frustrations at a toxic workplace. The hugely positive reviews come from the social media, marketing, and HR teams desperately trying to hide the fact that you'll be working for Satan, and spending your days kicking puppies.
Have a read through the reviews of working at Canonical here: https://www.glassdoor.co.uk/Reviews/Canonical-Reviews-E230560.htm
They are pretty damning, highlighting a clique-y and out-of-touch leadership team with a toxic workplace. There's a clear and consistent message about the company culture and the quality of the leadership team and management, and equally clearly, this feedback is being ignored. The reviews touch on many of the things that I've highlighted just by digging through the application process.
It doesn't have to be this way
Companies like Canonical are continuing to sabotage their efforts to hire security talent. The galling thing is that none of this is difficult to solve, and none of the solutions are cryptic, or secret esoteric knowledge senior cybersecurity people have been jealously guarding. We've all been talking about this for years.
- Stop asking for degrees. The only, ever, acceptable time to ask for a degree is for a senior position, where asking for "a cybersecurity degree, or equivalent professional experience" is the only right way to do it.
- Ask for certificates where they are relevant. CISSP for an entry-level analyst role? Do one. CISSP for a senior architect with 8-10 years of experience? Absolutely.
- The people responsible for managing the position should write the job description. They know what skills and experience matter.
- Keep the hiring pipeline short and simple. 3 interviews, max, run by people who will be managing the position and understand what is involved. Don't let people unrelated to managing the role do anything with the JD apart from adding some boilerplate fluff about how amazing your company is to work for.
- Interview candidates properly. None of this "yes/no" nonsense and questions that can easily be Googled. Use case studies, give the candidate a chance to show off their strengths, and have a conversation rather than an interrogation. And, above all, expect difficult questions from candidates, and actually answer them.
In Closing
No surprise why this role is unfilled almost a year after I first saw it posted. Normally, I'd look at a car crash like this and think "This is a company that isn't just not serious about hiring - they actively hate the sort of people who would apply."
But in reality, not only is this masterclass in how not to advertise a role, but this is an example of the current thinking and approach of too many companies. Companies that don't respect applicants, let alone their employees. Companies that don't value people's time. Companies that don't value the unique skills and expertise their employees bring to the table.
Ultimately, companies that are going to be in the news in the coming years for inexcusable and wholly avoidable security breaches.
I have nothing personally against Canonical - Ubuntu is mediocre but usable, they have had some major privacy slips, and Mark Shuttleworth is a dick - but their whole approach is a perfect example of everything that is currently wrong with hiring security talent.
I can only hope that sometime soon, as the breaches pile up, the idiots running companies like this will be held accountable.
Until then, have fun in your job hunting.